Uncovering Vulnerabilities: Professional Penetration Testing by MicroAntix Networks
In the evolving cyber threat landscape, merely having security controls in place isn’t enough. You need to know if they truly stand up to real-world attacks. At MicroAntix Networks, we offer professional Penetration Testing services, acting as ethical hackers to meticulously probe your systems, applications, and networks for exploitable vulnerabilities before malicious actors can find them. For businesses in the British Virgin Islands, this proactive approach is crucial for protecting sensitive data, ensuring business continuity, and upholding trust.
Our penetration testing services go beyond automated vulnerability scans. We simulate real-world attack scenarios, employing the same tactics, techniques, and procedures (TTPs) used by cybercriminals. This human-driven approach provides a realistic assessment of your security posture, identifying weaknesses that automated tools often miss and helping you understand the true impact of a potential breach.
Why is Professional Penetration Testing Crucial for Your BVI Business?
- Proactive Vulnerability Discovery: Identify and fix security weaknesses before malicious hackers can exploit them.
- Validation of Security Controls: Confirm that your existing firewalls, intrusion detection systems, antivirus, and other security measures are effective.
- Risk Prioritization: Receive actionable insights that categorize vulnerabilities by severity and potential business impact, allowing you to prioritize remediation efforts.
- Compliance Adherence: Meet regulatory requirements (e.g., PCI DSS, GDPR, local BVI data protection laws) that often mandate regular penetration testing.
- Enhanced Security Posture: Gain a realistic understanding of your organization’s resilience against cyberattacks and develop a stronger, more targeted security strategy.
- Protection of Reputation & Trust: Proactively prevent data breaches that can severely damage your brand reputation and erode customer trust in the competitive BVI market.
- Business Continuity: Identify potential attack paths that could lead to downtime or operational disruption, helping you fortify your defenses and ensure uninterrupted service.
MicroAntix Networks: Our Professional Penetration Testing Methodology
MicroAntix employs a structured and ethical approach to penetration testing, ensuring a thorough assessment with minimal disruption to your operations. Our certified ethical hackers adhere to industry best practices and standards (e.g., OWASP, NIST, PTES).
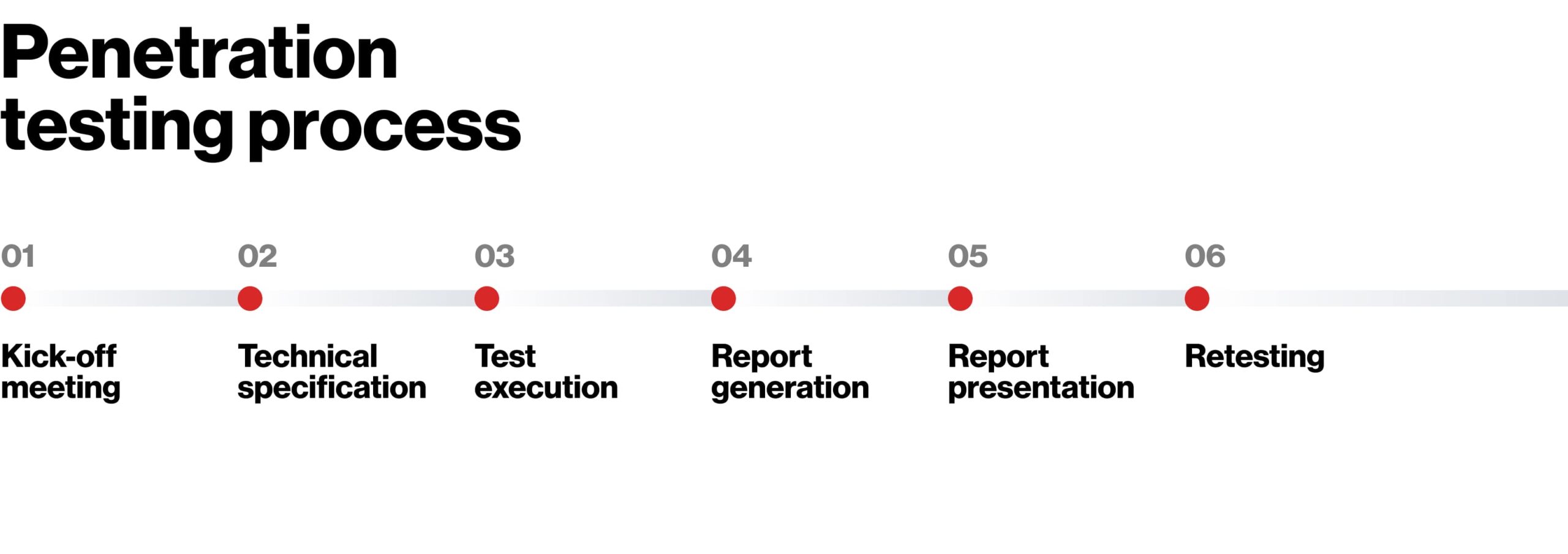
Our Comprehensive Penetration Testing Process:
-
Planning & Reconnaissance:
- Scope Definition: Working closely with your team, we define the scope of the test, including targets (networks, applications, physical), testing type (black-box, white-box, gray-box), and permissible techniques.
- Information Gathering: Our testers gather information about your organization and its systems using publicly available data (OSINT) and, depending on the test type, internal documentation provided by you.
-
Scanning & Vulnerability Analysis:
- Automated Scanning: We use industry-leading tools to identify known vulnerabilities, open ports, and misconfigurations.
- Manual Analysis: Our experts manually analyze the scan results, filtering out false positives and diving deeper into potential weaknesses that automated tools might overlook.
-
Exploitation:
- Simulated Attack: Our ethical hackers attempt to exploit identified vulnerabilities to gain unauthorized access, escalate privileges, or extract sensitive data. This phase simulates real-world attack scenarios to demonstrate actual risk.
- Impact Assessment: We assess the potential impact of a successful exploit on your business, including data exposure, system downtime, and potential lateral movement within your network.
-
Reporting & Remediation Guidance:
- Detailed Report: You receive a comprehensive report outlining all discovered vulnerabilities, their severity, the methods used to exploit them, and the potential business impact. Screenshots and proof-of-concept are included.
- Actionable Recommendations: Crucially, the report provides clear, prioritized, and actionable recommendations for remediating each vulnerability, including technical fixes and strategic security improvements.
- Debriefing: We conduct a debriefing session to walk through the findings, answer your questions, and help your team understand the remediation steps.
-
Retesting (Optional):
- After you implement the recommended fixes, we can perform retesting to verify that the vulnerabilities have been successfully remediated and no new issues have been introduced.
Types of Penetration Testing Offered by MicroAntix Networks
We offer a range of specialized penetration testing services to cover all aspects of your digital footprint:
- Network Penetration Testing (Internal & External):
- External: Simulates an attacker trying to breach your public-facing systems (firewalls, routers, web servers, email servers) from the internet.
- Internal: Simulates an attack from within your network (e.g., a rogue employee, a compromised insider, or an attacker who has already gained initial access), assessing lateral movement capabilities and internal system vulnerabilities.
- Web Application Penetration Testing:
- Evaluates the security of your web-based applications (e.g., e-commerce sites, client portals, internal web apps) for vulnerabilities like SQL injection, cross-site scripting (XSS), broken authentication, and insecure APIs, as per OWASP Top 10.
- Mobile Application Penetration Testing:
- Assesses the security of your Android and iOS mobile applications, focusing on data storage, authentication, API security, and potential client-side vulnerabilities.
- Wireless Penetration Testing:
- Evaluates the security of your Wi-Fi networks (e.g., WPA2/WPA3 configurations, rogue access points, guest networks) to ensure unauthorized access is prevented.
- Cloud Penetration Testing:
- Assesses the security configurations and deployed applications within your cloud environments (e.g., Azure, AWS, Google Cloud), ensuring proper access controls, data segregation, and secure workload deployment.
- Social Engineering Penetration Testing:
- Simulates human-centric attacks like phishing, vishing (voice phishing), and physical pretexting to test your employees’ security awareness and the effectiveness of your security policies. (Often integrated with Security Awareness Training).
- Physical Penetration Testing:
- (Performed upon specific request and scope) Simulates attempts to gain unauthorized physical access to your facilities, data centers, or sensitive areas, testing access controls, surveillance, and security personnel response.

